A security vulnerability has been discovered in the USB-C port controller fitted to the iPhone 15 and 16. However, exploiting it would be so complex that both Apple and the security researcher who discovered it concluded that it is not a real-world threat.
However, a security concern that does pose a threat to iPhone users is a tactic scammers are using to bypass one of Apple’s built-in protections …
Security vulnerability in iPhone’s USB-C port
Security researcher Thomas Roth discovered a vulnerability in the USB-C controller chip first introduced into Apple’s supply chain in 2023. In principle, it could be used to compromise an iPhone, as Cyber Security News reports.
Security researchers have successfully hacked Apple’s proprietary ACE3 USB-C controller. This chip, introduced with the iPhone 15 and iPhone 15 Pro, represents a significant leap in USB-C technology, handling power delivery and acting as a sophisticated microcontroller with access to critical internal systems […]
[Roth’s team was able] to gain code execution on the ACE3 chip. By carefully measuring electromagnetic signals during the chip’s startup process, they identified the precise moment when firmware validation occurred.
Using electromagnetic fault injection at this critical juncture, they successfully bypassed the validation checks and booted a modified firmware patch into the chip’s CPU.
In theory, this could give an attacker complete control over an iPhone.
However, it would require physical access to the device, and is exceedingly difficult to pull off. Macworld reports that Apple concluded it wasn’t a realistic threat after examining the method used, and Roth agreed.
Tactic by iMessage scammers can bypass protections
SMS and iMessages are commonly used by scammers to send links intended to carry out phishing attacks, and to attempt to instal malware in iPhones.
To protect against this, if you receive an iMessage from someone who is not in your contacts, and with whom you’ve never exchanged messages, your iPhone automatically disables any links in the message. They appear as plain text, and cannot be tapped.
However, scammers have found a way around this. If they can convince you to reply to the message, even with a STOP command intended to instruct a legitimate sender not to message you again, then this protection is disabled.
BleepingComputer says the fact that you have messaged them, even with a one-character reply, means the iPhone considers them legitimate and unblocks their links.
Apple told BleepingComputer that if a user replies to that message or adds the sender to their contact list, the links will be enabled.
Over the past couple of months, BleepingComputer has seen a surge in smishing attacks that attempt to trick users into replying to a text so that links are enabled again.
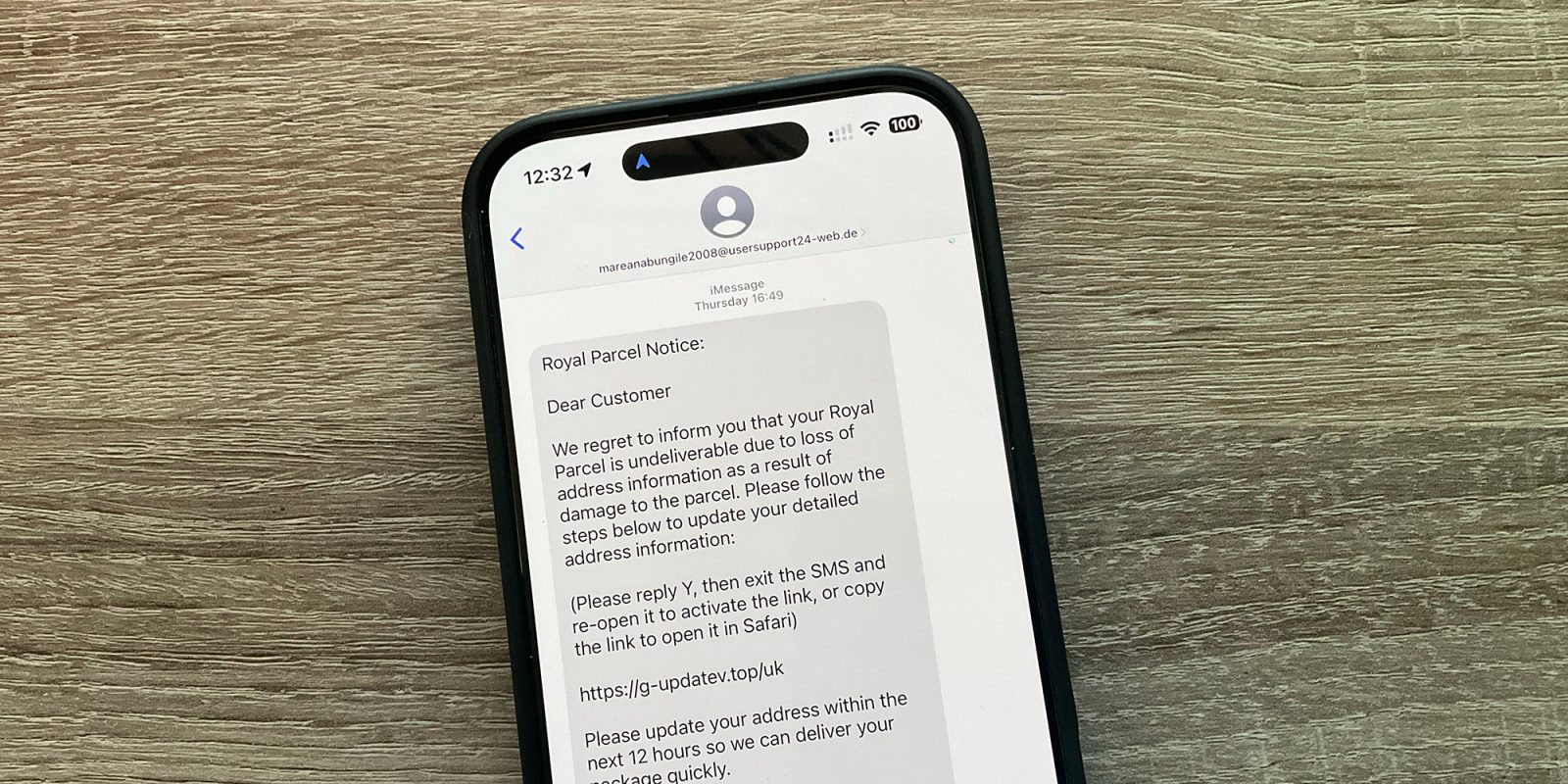
The site showed examples of fake texts claiming to be from USPS and a toll road company, each asking the recipient to reply with Y. This would activate the links.
It’s common enough that I was able to find the above example to photograph simply by looking in my deleted messages folder.
How to protect yourself
Never tap or click a link received in an email or other message unless you are expecting it. Best practice is to only ever use your own bookmarks or type URLs manually, and only do the latter if you have good reason to think the message genuine. When in doubt, call or message the company using known contact details to verify.
- Here’s how to protect against iPhone password reset attacks
- Apple shares how to protect your Apple ID, avoid phishing and other scams
Photo: 9to5Mac
FTC: We use income earning auto affiliate links. More.

 11 hours ago
2
11 hours ago
2








![YouTube Music fixes Top Listener badge for December 2024 [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/03/youtube-music-logo-2.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)










 English (US) ·
English (US) ·