Users who are simply looking to download the world’s most popular web browser may accidentally be infecting their systems with malware, says a new report from Malwarebytes Labs.
Called SecTopRAT, the malware hides inside a malicious ad that purports to be an installer for Google Chrome. However, anyone who clicks on the ad is instead funneled to a fake Google website designed to cleverly mimic the legitimate page. A final redirect downloads a large executable file that is disguised as the Chrome download but also includes the SecTopRAT malware.
The installer connects and retrieves all the necessary instructions, including requests to run as an admin in order to perform particular tasks. A PowerShell command adds an exclusion path so Windows Defender won’t be triggered when the malware is extracted from the download.
The malicious code is injected into the legitimate download process, so Google's Chrome browser itself is still downloaded as usual; the user doesn’t suspect that anything is happening. SecTopRAT is a remote access Trojan with stealer capabilities so it prefers to operate in the background without being noticed.
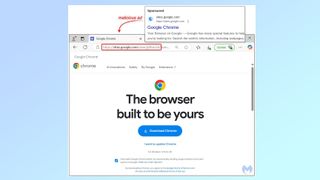
Much like the massive Google account phishing campaign seen earlier this year, the hackers have gone through great lengths to get their fake website to resemble the actual Google page. When searching for “download google chrome” the URL in the sponsored result for the fake page is “https://sites.google.com” which is actually the web address for Google’s free website builder.
It is particularly egregious that the hackers behind this campaign used the company's free website builder to build a look-a-like page to infect unsuspecting users. However, since all pages with a sites.google.com address are user generated and part of an open platform, they can easily be confused with pages generated by Google itself.
How to stay safe
Malwarebytes points out in its report that its security software was able to protect users from this attack, so having antivirus software installed and up to date on your system is of absolute necessity to protect yourself from very convincing attacks like this one. At the same time, you also want to be aware of the most common phishing attack techniques and methods, know where to go to acquire software safely and never click on (or scan) unexpected links, PDFs or QR codes.
The increasing use of AI and malware as a service style attacks mean it's increasingly difficult for users to distinguish between legitimate sites and emails and malicious ones, so having one of the best antivirus software suites on your PC is a must.
You’re also going to want to make sure that you always enable multi-factor authentication whenever possible, use a password manager to protect your online accounts, and especially when provided by your antivirus suite, use a VPN.
Since Google Chrome is by far the most popular browser, attacks like this one will likely keep occurring as it's easy for hackers to impersonate the search giant. Hopefully though, Google begins cracking down on malicious ads further and making it more difficult for hackers and other cybercriminals to buy ad space in the first place.
More from Tom's Guide
- Chase will start blocking Zelle payments to social media accounts — here's why
- Help improve Tom's Guide — your chance to win a $250 Amazon gift card
- Google Docs under attack from info-stealing malware — how to keep your data and your emails safe



















 English (US) ·
English (US) ·